Are you being phished?
Over the last several months Mines has seen a dramatic increase in the quality of the email-based attacks targeting our employees and students. This new wave of sophisticated scams (known as “phishing“) is significantly more difficult to identify compared to previous generations of attacks. This is due in large part to the time those perpetrating these attacks are spending doing research about their targets.
As a result of this research, the attacks are tailored to mimic communications we are accustom to receiving. Messages appear to come from our friends or colleagues, or contain details about our personal life, research interests, and professional environment. The seemingly legitimate nature of the messages makes them almost impossible to detect with traditional technical solutions, meaning that we as recipients need to be extra-vigilant. To help with that effort my office would like to recommend the following:

- Remember that anyone can put any address in the From: field of an email. Just because the email says it is from JaneDoe@mines.edu does not mean the message is from Jane, or even that it originated at Mines. To combat this always double check the email address in the To: field of any reply. Is it going where you expect it to go?
- Be cognizant of what information is publicly available about you and be careful not to assume that the author of a message knows you simply because they know something about you. Maybe they just looked at your Facebook or LInkedIn page.
- Similarly, be aware of information that might have been released about you in any of the recent disclosures by public companies. An email from a professional society following up about an out-of-town conference you recently attended could simply be a combination of your Marriott hotel reservations and the list of memberships on your personal web page.
- Remember that no one at Mines should ever send an email with a link that requests you to enter your username and password. You should know what the institution’s federated identity login pages look like and should never use your Mines password on any other site.
- Sign up for the school’s Multi-Factor Authentication (MFA) program.
- Most importantly, if you have the slightest doubt about the legitimacy of a message, ask the sender for verification and/or send the message to ITS. We in ITS would much rather check 100 valid messages than see one person compromised after responding to a malicious message. You can report a suspicious message by forwarding it to phishing@mines.edu.
As always, please feel free to reach out to me or my staff if you have any questions at all, via a Mines Help Center support request (https://helpcenter.mines.edu) or an email to security@mines.edu.
Susan McMillin
Chief Information Security Officer
Colorado School of Mines
(303) 384-2699
Examples of real Mines login screens
When logging into Mines resources via the web, you will see authentic screens like these. To make sure you are communicating with a Mines login server, check the web address (the URL) at the top of the page to make sure the link has “mines.edu” at its root.
“Shibboleth” Login Screen
You’ll see this login screen when accessing many Mines online services with your MultiPass credentials.
Note that the address bar in your browser shows a legitimate URL beginning like this: https://idp.mines.edu/…
That tells you that you’re on the mines.edu server that handles such logins.

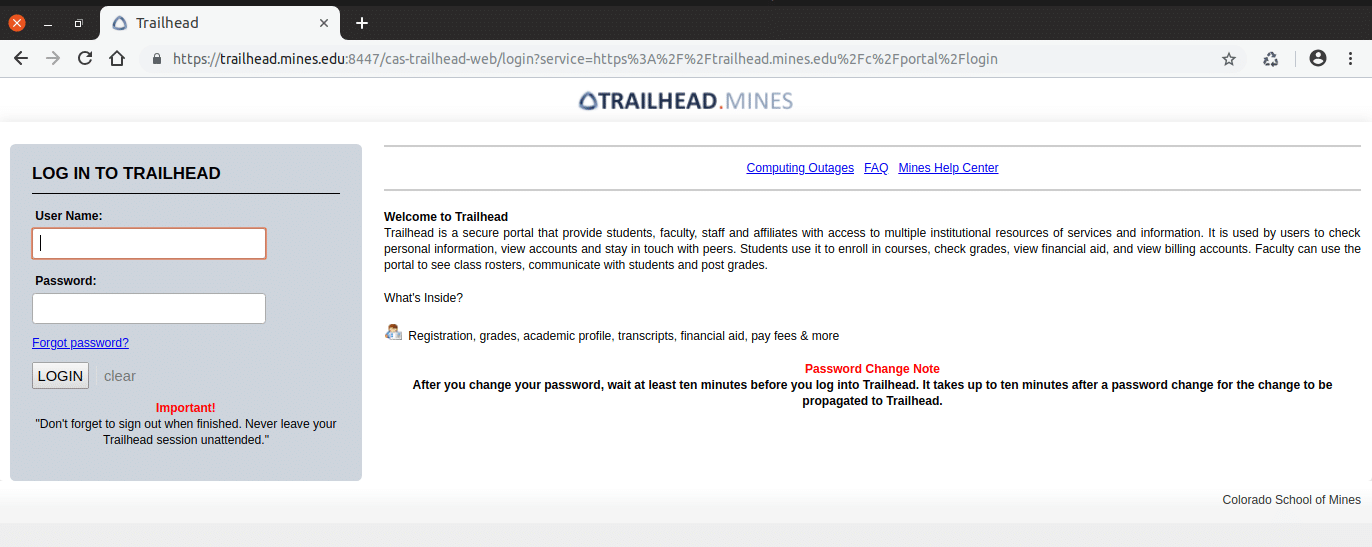
Trailhead Login Screen
You’ll see this login screen when accessing the Mines Trailhead portal with your MultiPass credentials.
Note that the address bar in your browser shows a legitimate URL beginning like this: https://trailhead.mines.edu/…
That tells you that you’re on the mines.edu server that houses the Trailhead portal.
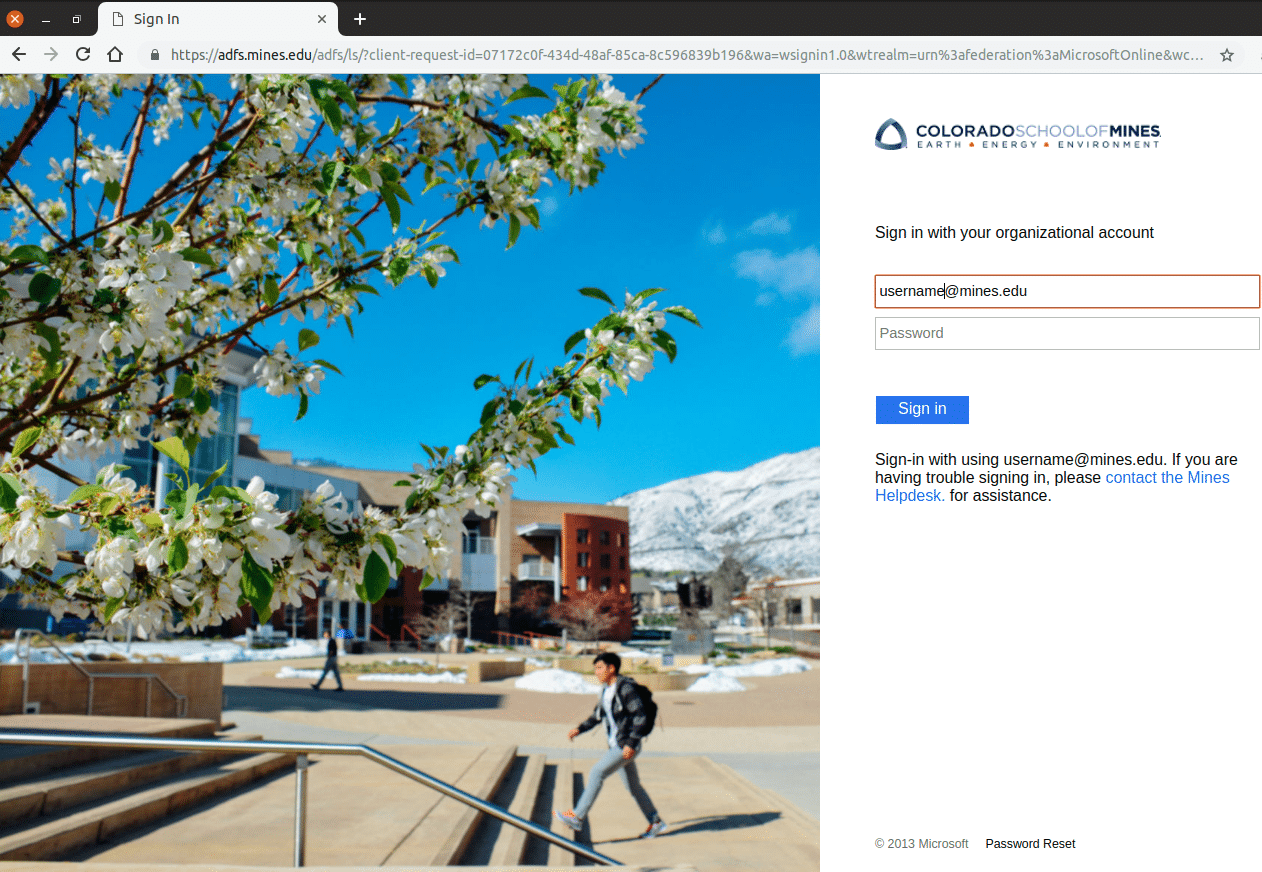
ADFS Login Screen
You’ll see this login screen when accessing Mines-specific Microsoft online services such as Outlook365 and Exchange Email in the cloud.
Note that the address bar in your browser shows a legitimate URL beginning like this: https://adfs.mines.edu/…
That tells you that you’re logging into Mines-branded Office365 using a mines.edu server that handles such logins. Your Mines MultiPass credentials are authenticated here — Microsoft will never have access to them.
(Note that you will be redirected to a Microsoft server after login, at a URL that starts with https://outlook.office365.com/owa/… That is normal.)